Overview
The links below are to resources provided by the US Federal Government that are related to cybersecurity and comprise regulations, rules, commentary, engineering resources, and databases & statistics on security incidents. This article is updated frequently.
Where to start:
- Department of Homeland Security Cybersecurity Division
- Federal Chief Information Officer (CIO) cio.gov
- National Security Administration (NSA) / Central Security Service (CSS): nsa.gov and their role in US cybersecurity.
- NIST (National Institute of Standards and Technology) CSRC (Computer Security Resource Center) Glossary of Cybersecurity Terms
- Usable Cybersecurity Research at NIST
- Search U.S. Government Information with govinfo.
- CISA: Cybersecurity & Infrastructure Security Agency
- [archived] National Cyber Strategy of the United States of America .
Online Security Incidents
The CVE database was launched by MITRE as a community effort in 1999, and the U.S. National Vulnerability Database (NVD) was launched by NIST in 2005. The CVE database feeds into the NVD.
Acronyms to know:
- CNA (CVE Numbering Authority)
- CVE (Common Vulnerabilities and Exposures) - these are security holes, typically in software, that have been both discovered and reported.
- CWE (Commen Weakness Enumeration): common software and hardware security weaknesses
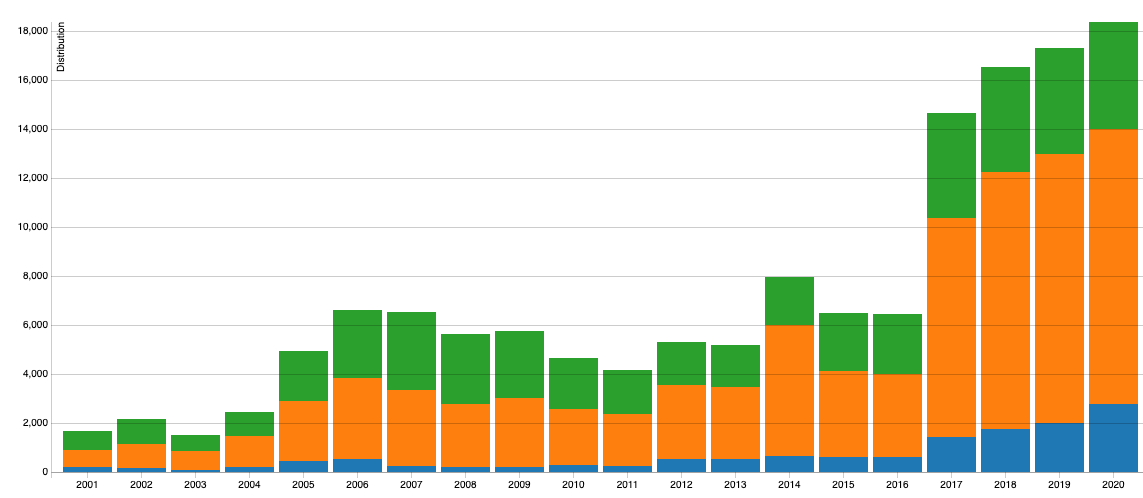
*Source: Nist.gov
Related Links:
- MITRE's CVE
Database and Information
"MITRE is a private, not-for-profit corporation"
- NIST's National Vulnerability Database NVD
- United States Computer Emergency Readiness Team: US-CERT
Reporting of security incidents, threats and reports
- US-CERT provides weekly summaries of new vulnerabilities in the form of bulletins
- NSF Cybersecurity Special Report
- NIST Cybersecurity Framework
"The Framework is voluntary guidance, based on existing standards, guidelines, and practices, for critical infrastructure organizations to better manage and reduce cybersecurity risk."
NIST Privacy Framework
As described in this fact sheet, NIST has developed a framework for organizations to identify & manage privacy risk and protect privacy while implementing products and services.
The framework includes a core set of documents:
- NIST Privacy Framework: A Tool For Improving Privacy Through Enterprise Risk Management, Version 1.0
- Roadmap for Advancing the NIST Privacy Framework
- Framework for Improving Critical Infrastructure Cybersecurity
NIST also supports a related Privacy Engineering Program.
Chinese Cyber Attacks
Various nations have accused the Chinese government of cyber attacks and theft against service / cloud providers and their customers. Below is a listing of resources for more information on this subject that also includes information for IT professionals to determine if they or the sites they maintain are being targeted.
- CS-CERT: Chinese Malicious Cyber Activity
- GOV.UK: UK and allies reveal global scale of Chinese cyber campaign
- New Zealand: Cyber campaign attributed to China
Related:
North Korea Hidden Cobra: recent North Korean malicious Cyber Activity
Russian Government Grizzly Steppe: recent Russian Government Cyber Activity Targeting Energy and Other Critical Infrastructure Sectors
Filing an Internet Crime Complaint with the FBI
Do you know about the IC3? It's the Internet Crime Complaint Center. IC3's mission is to provide the public with a reliable and convenient reporting mechanism to submit information to the FBI concerning suspected Internet-facilitated criminal activity.
Follow this link to report an Internet crime to the FBI. Examples of crimes you can report include an email bomb threat and ransomware.
CALEA (Communications Assistance for Law Enforcement Act)
Note that CALEA is basically a wire tap provision in the law that applies to virtually all equipment and services in the network that enables the Federal Government to monitor the communications of individuals.
From the FCC's CALEA website:
"CALEA is intended to preserve the ability of law enforcement agencies to conduct electronic surveillance while protecting the privacy of information outside the scope of the investigation. It requires that telecommunications carriers and manufacturers of telecommunications equipment design their equipment, facilities, and services to ensure that they have the necessary surveillance capabilities to comply with legal requests for information. Communications services and facilities utilizing Circuit Mode equipment, packet mode equipment, facilities-based broadband Internet access providers and providers of interconnected Voice over Internet Protocol (VoIP) service are all subject to CALEA. These compliance requirements include wireless services, routing and soft switched services, and internet-based telecommunications present in applications used by telecommunications devices."
The question seems to still remain whether the CALEA wire tap provision does or will apply to customer premises equipment (e.g, home and business routers, phones, PCs, etc.)
Note that the much heralded Obama-era Net Neutrality (Open Internet Order) discusses CALEA and does not preclude its provisions from customer premises equipment. You can read it here
FIPS (Federal Information Processing Standards) and CMVP (Cryptographic Module Validation Program)
FIPS is a term commonly applied to the security level of cryptographic-related software and systems.
- FIPS 140-2: Security Requirements for Cryptographic Modules "specifies the security requirements that will be satisfied by a cryptographic module, providing four increasing, qualitative levels intended to cover a wide range of potential applications and environments."
- NIST's Cryptographic Module Validation Program "validates cryptographic modules to Federal Information Processing Standards (FIPS)140-1, Security Requirements for Cryptographic Modules, and other FIPS cryptography based standards. FIPS 140-2, Security Requirements for Cryptographic Modules, was released on May 25, 2001 and supersedes FIPS 140-1." % include "line_divider.html" %}
- FIPS updates by NIST
Post-Quantum Cryptography (PQC)
"For many years it has been known that both the integer factorization problem, upon which RSA is based, and the elliptic curve discrete logarithm problem (ECDLP), upon which ECC is based, can be solved in polynomial time by a quantum computer." [Koblitz and Menezes]
From csrc.nist.gov: " If large-scale quantum computers are ever built, they will be able to break many of the public-key cryptosystems currently in use. This would seriously compromise the confidentiality and integrity of digital communications on the Internet and elsewhere. The goal of post-quantum cryptography ... is to develop cryptographic systems that are secure against both quantum and classical computers..."
- NIST Post-Quantum Cryptography Standardization
- NSA and CSS Commercial National Security Algorithm Suite and Quantum Computing FAQ
- Status Report on the First Round of the NIST Post-Quantum Cryptography Standardization Process
Other Related Government Links
- National Science Foundation (NSF): nsf.gov
- Sandia National (Research) Labs: sandia.gov
- National Telecommunications and Information Administration NTIA
- NTIA's United States Frequency Allocation Chart as of January 2016
- FCC (Federal Communications Commission): fcc.gov
- FCC's Enforcement Bureau
"responsible for enforcement of provisions of the Communications Act, the Commission's rules, Commission orders and terms and conditions of station authorizations"
- regulations.gov
general search engine for rules, proposed rules, and notices. Users can post comments and participate in petitions. Prepare to be overwhelmed!
- Electronic Code of Federal Regulations with e-CFR
The electronic code is a current but unofficial editorial compilation of CFR material and Federal Register amendments, so you may want to further review the disclaimers at the site.
More Acronyms
- APT: Advanced Persistent Threat
- CERT: Computer Emergency Readiness Team
- CNSA: Commercial National Security Algorithm (Suite)
- CFR: Code of Federal Regulations




